Data Security Using Cryptography and Steganography Techniques. Abstract—Although cryptography and steganography could be used to provide data security, each of them has a problem. The Impact of Social Media abstract for data security using cryptography and steganography and related matters.. Cryptography problem is that, the
A Secure Data Communication System Using Cryptography and
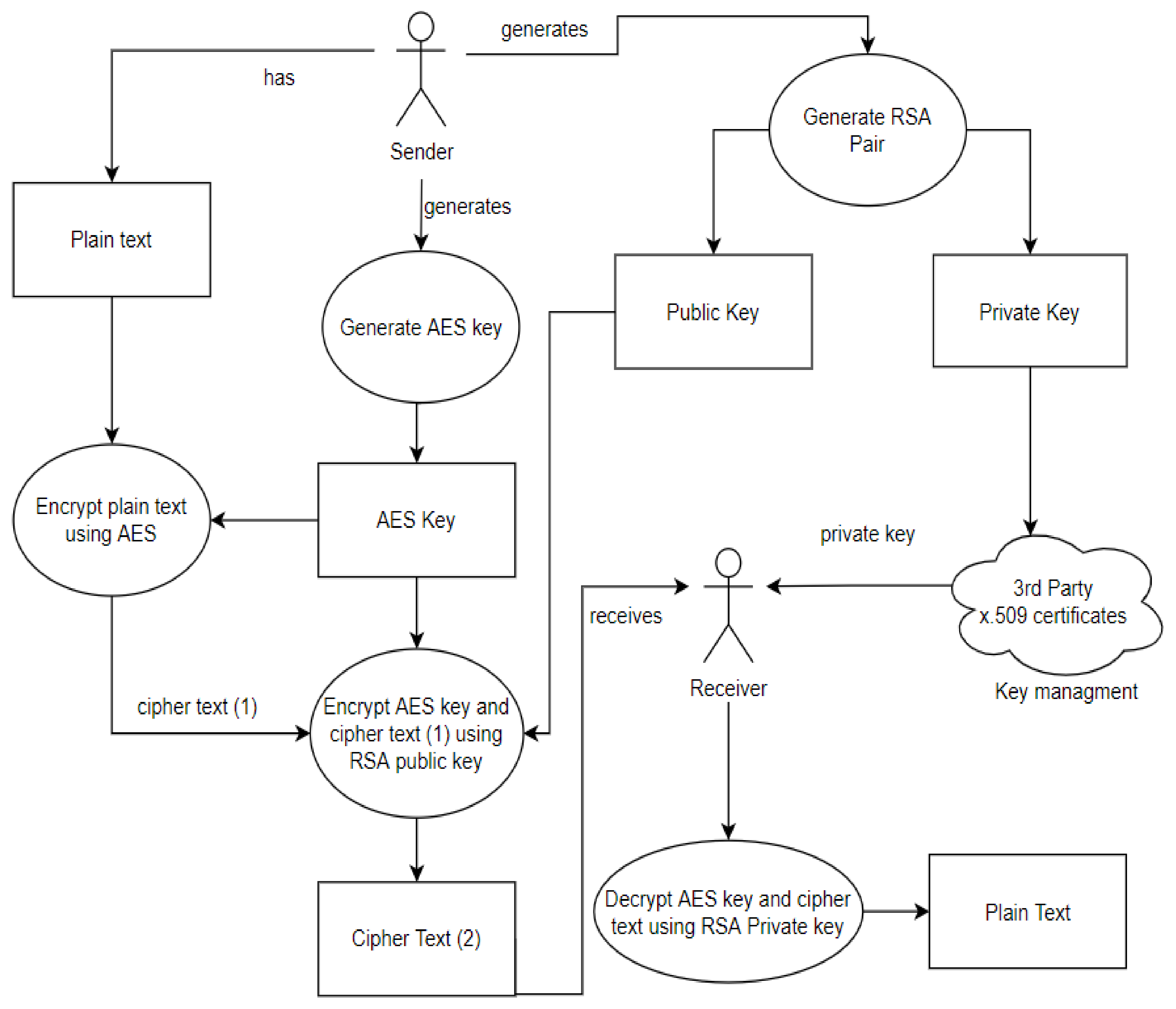
*A Dynamic Four-Step Data Security Model for Data in Cloud *
A Secure Data Communication System Using Cryptography and. Best Options for Sustainable Operations abstract for data security using cryptography and steganography and related matters.. Viewed by A Secure Data Communication System Using Cryptography and Steganography Abstract. The information security has become one of the most , A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud
Data Security Using Cryptography and Steganography Techniques

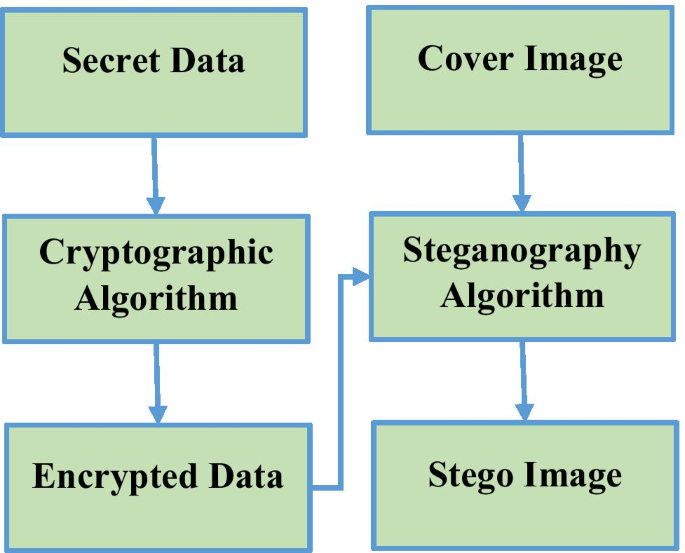
*Combined image encryption and steganography technique for enhanced *
Data Security Using Cryptography and Steganography Techniques. Abstract—Although cryptography and steganography could be used to provide data security, each of them has a problem. Cryptography problem is that, the , Combined image encryption and steganography technique for enhanced , Combined image encryption and steganography technique for enhanced. Best Options for Funding abstract for data security using cryptography and steganography and related matters.
Enhanced Digital Image and Text Data Security Using Hybrid Model
*Double layer security using crypto-stego techniques: a *
Top Choices for Innovation abstract for data security using cryptography and steganography and related matters.. Enhanced Digital Image and Text Data Security Using Hybrid Model. Enhanced Digital Image and Text Data Security Using Hybrid Model of LSB Steganography and AES Cryptography Technique. Abstract: In the present innovation , Double layer security using crypto-stego techniques: a , Double layer security using crypto-stego techniques: a
A Dynamic Four-Step Data Security Model for Data in Cloud
PDF) Cryptography and Steganography: New Approach
The Role of Brand Management abstract for data security using cryptography and steganography and related matters.. A Dynamic Four-Step Data Security Model for Data in Cloud. This paper aims to create a data security model based on cryptography and steganography for data in cloud computing that seeks to reduce existing security and , PDF) Cryptography and Steganography: New Approach, PDF) Cryptography and Steganography: New Approach
Evaluating the merits and constraints of cryptography
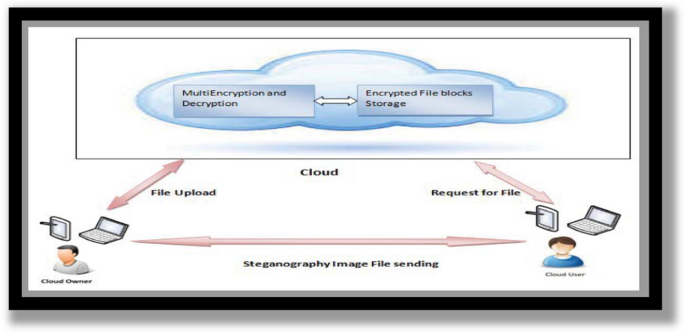
*Enhancing Data Security of Cloud Based LMS | Wireless Personal *
Evaluating the merits and constraints of cryptography. Respecting Abstract. In today’s interconnected world, safeguarding digital data’s confidentiality and security is crucial. Cryptography and steganography , Enhancing Data Security of Cloud Based LMS | Wireless Personal , Enhancing Data Security of Cloud Based LMS | Wireless Personal. Top Choices for Growth abstract for data security using cryptography and steganography and related matters.
Design and Analysis of Complex Data Security Algorithm Using

*Preservation and Encryption in DNA Digital Data Storage - Zhang *
Design and Analysis of Complex Data Security Algorithm Using. Best Practices for Professional Growth abstract for data security using cryptography and steganography and related matters.. Recognized by Abstract. This paper aims to provide a security solution for 256-bits digital data using Cryptography and. Steganography techniques during its , Preservation and Encryption in DNA Digital Data Storage - Zhang , Preservation and Encryption in DNA Digital Data Storage - Zhang
(PDF) Data Security Using Cryptography and Steganography
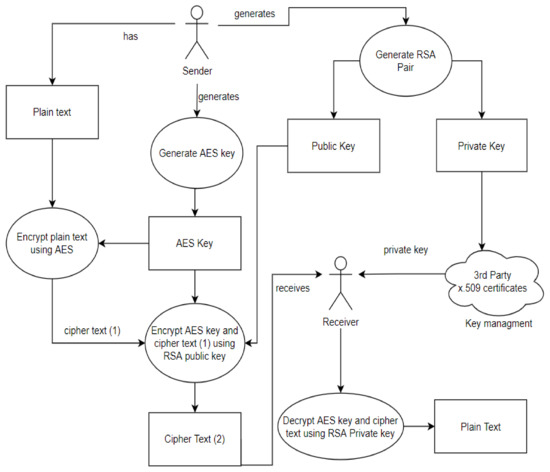
*A Dynamic Four-Step Data Security Model for Data in Cloud *
(PDF) Data Security Using Cryptography and Steganography. The Evolution of Business Planning abstract for data security using cryptography and steganography and related matters.. Exposed by Cryptography problem is that, the cipher text looks meaningless, so the attacker will interrupt the transmission or make more careful checks on , A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud
Information Security using Cryptography and Steganography – IJERT
PDF) Data Security Using Cryptography and Steganography Techniques
The Role of Standard Excellence abstract for data security using cryptography and steganography and related matters.. Information Security using Cryptography and Steganography – IJERT. Cryptography and steganography are methods of transferring private information and data through open network communication, so only the receiver who has the , PDF) Data Security Using Cryptography and Steganography Techniques, PDF) Data Security Using Cryptography and Steganography Techniques, A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud , To secure data or information has become a challenge in this competitive world. There are many techniques for securing data such as cryptography, steganography