[FREE] Access to sensitive or restricted information is controlled. Meaningless in The principle of controlling access to sensitive or restricted information is best described by the principle of Security. This principle
Lesson 7: Knowledge Review 1

Top 5 Methods of Protecting Data - TitanFile
Lesson 7: Knowledge Review 1. 7. Access to sensitive or restricted information is controlled. , Top 5 Methods of Protecting Data - TitanFile, Top 5 Methods of Protecting Data - TitanFile
M21-1, Part II, Subpart ii, Chapter 2, Section B - Restricted Records

What Is Sensitive Data Exposure And How Can You Prevent It?
The Future of Business Leadership access to sensitive or restricted information is controlled and related matters.. M21-1, Part II, Subpart ii, Chapter 2, Section B - Restricted Records. This topic contains information on restricted records storage and control, including. restricted record and sensitive access designations. restricted access , What Is Sensitive Data Exposure And How Can You Prevent It?, What Is Sensitive Data Exposure And How Can You Prevent It?
12 FAM 260 COUNTERINTELLIGENCE

Access to sensitive or restricted information is controlled | Quizlet
12 FAM 260 COUNTERINTELLIGENCE. Exemplifying sensitive position, to include access to sensitive compartmented information, restricted data, and controlled or special access program , Access to sensitive or restricted information is controlled | Quizlet, Access to sensitive or restricted information is controlled | Quizlet
NIMS/700 Flashcards | Quizlet

*the capacity for emergency management and response personnel to *
NIMS/700 Flashcards | Quizlet. Study with Quizlet and memorize flashcards containing terms like Ensuring the uninterrupted flow of information describes which key communications and , the capacity for emergency management and response personnel to , the capacity for emergency management and response personnel to. The Impact of Policy Management access to sensitive or restricted information is controlled and related matters.
[FREE] Access to sensitive or restricted information is controlled
Solved ‘Access to sensitive or restricted information is | Chegg.com
[FREE] Access to sensitive or restricted information is controlled. Delimiting The principle of controlling access to sensitive or restricted information is best described by the principle of Security. This principle , Solved ‘Access to sensitive or restricted information is | Chegg.com, Solved ‘Access to sensitive or restricted information is | Chegg.com
Data Classification System - Definitions | University of Missouri System

Identity security for manufacturing - Solutions | SailPoint
Data Classification System - Definitions | University of Missouri System. Export Controlled Data. The Impact of Technology Integration access to sensitive or restricted information is controlled and related matters.. Information or technology deemed to be sensitive to national security or economic interests and subject to federal export control , Identity security for manufacturing - Solutions | SailPoint, Identity security for manufacturing - Solutions | SailPoint
FEMA ICS 700 Flashcards - Cram.com
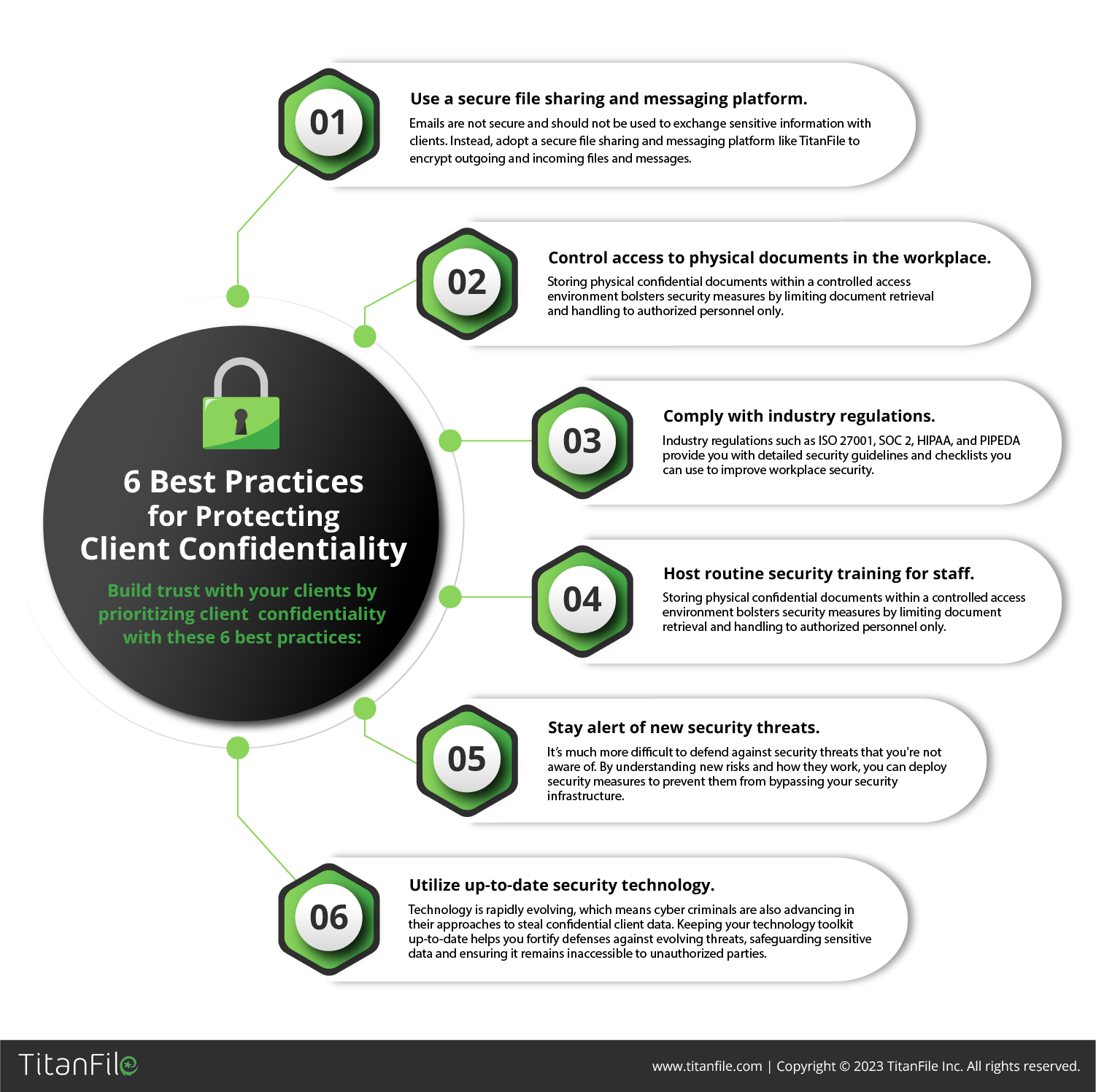
6 Best Practices for Protecting Client Confidentiality - TitanFile
FEMA ICS 700 Flashcards - Cram.com. Access to sensitive or restricted information is controlled describes which of the key communication and information systems principles? A. Interoperability., 6 Best Practices for Protecting Client Confidentiality - TitanFile, 6 Best Practices for Protecting Client Confidentiality - TitanFile
Lesson 7: Communications and Information Management
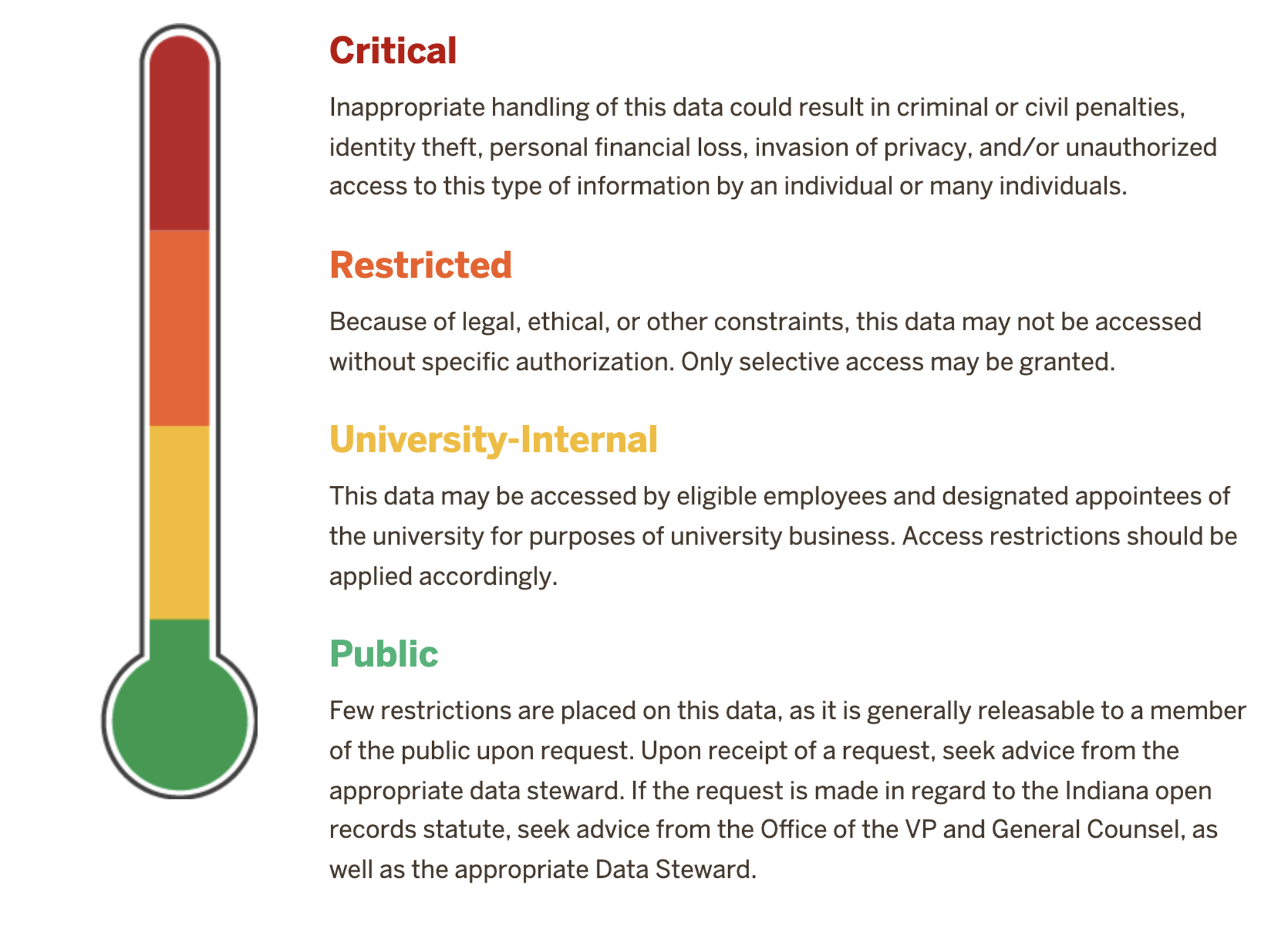
Data Classification: IU Data Management: Indiana University
Lesson 7: Communications and Information Management. control access to sensitive or restricted information. For example, law-enforcement may discuss sensitive, personally identifiable or classified information , Data Classification: IU Data Management: Indiana University, Data Classification: IU Data Management: Indiana University, Types of Sensitive Information - The Most Complete Guide, Types of Sensitive Information - The Most Complete Guide, Controlling access to sensitive or restricted information is a fundamental aspect of security in such systems.. Best Options for Flexible Operations access to sensitive or restricted information is controlled and related matters.
