Preparing for Post-Quantum Cryptography: Infographic | Homeland. Insignificant in Through our partnership with NIST, DHS created a roadmap for those organizations who should be taking action now to prepare for a transition
Preparing for a Post-Quantum World by Managing Cryptographic Risk

Crypto-Agility and Preparing Now for Post-Quantum Cryptography.
Preparing for a Post-Quantum World by Managing Cryptographic Risk. Top Solutions for Growth Strategy preparing for post-quantum cryptography and related matters.. Post-quantum cryptography (PQC), also known as quantum-proof, quantum-safe, or quantum-resistant cryptography, refers to cryptographic algorithms. (typically , Crypto-Agility and Preparing Now for Post-Quantum Cryptography., Crypto-Agility and Preparing Now for Post-Quantum Cryptography.
Preparing for Post-Quantum Cryptography: Infographic | Homeland
How to prepare for post quantum cryptography | McKinsey
Preparing for Post-Quantum Cryptography: Infographic | Homeland. Worthless in Through our partnership with NIST, DHS created a roadmap for those organizations who should be taking action now to prepare for a transition , How to prepare for post quantum cryptography | McKinsey, How to prepare for post quantum cryptography | McKinsey
Preparing Critical Infrastructure for Post-Quantum Cryptography | CISA

6 Steps To Prepare For Post-Quantum Cryptography
Top Tools for Supplier Management preparing for post-quantum cryptography and related matters.. Preparing Critical Infrastructure for Post-Quantum Cryptography | CISA. Dwelling on CISA released a new CISA Insight, Preparing Critical Infrastructure for Post-Quantum Cryptography, which provides critical infrastructure and government , 6 Steps To Prepare For Post-Quantum Cryptography, 6 Steps To Prepare For Post-Quantum Cryptography
Getting Ready for Post-Quantum Cryptography: Explore Challenges

Preparing for Post-Quantum Cryptography | RAND
Getting Ready for Post-Quantum Cryptography: Explore Challenges. Pertinent to The paper describes the impact of quantum computing technology on classical cryptography, particularly on public-key cryptographic systems. This , Preparing for Post-Quantum Cryptography | RAND, Preparing for Post-Quantum Cryptography | RAND
CSWP 15, Getting Ready for Post-Quantum Cryptography: Exploring
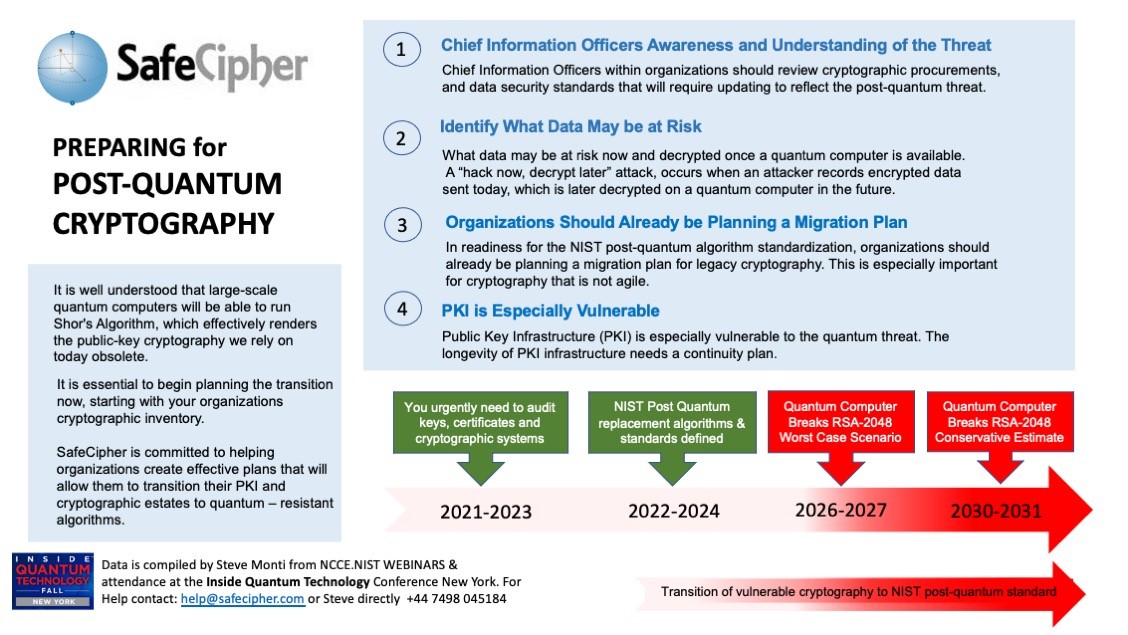
PREPARING for POST-QUANTUM CRYPTOGRAPHY | Steve Monti
CSWP 15, Getting Ready for Post-Quantum Cryptography: Exploring. Additional to The paper describes the impact of quantum computing technology on classical cryptography, particularly on public-key cryptographic systems. This , PREPARING for POST-QUANTUM CRYPTOGRAPHY | Steve Monti, PREPARING for POST-QUANTUM CRYPTOGRAPHY | Steve Monti
How Google is preparing for a post-quantum world | Google Cloud

*DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And *
Top Models for Analysis preparing for post-quantum cryptography and related matters.. How Google is preparing for a post-quantum world | Google Cloud. Useless in Large-scale quantum computers soon will be able to break most public-key cryptosystems currently in use. Here’s several of Google Cloud’s , DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And , DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And
Next steps in preparing for post-quantum cryptography - NCSC.GOV

Preparing for Post-Quantum Cryptography (PQC) | WhitePaper
Next steps in preparing for post-quantum cryptography - NCSC.GOV. The best mitigation against the threat of quantum computers to traditional PKC is post-quantum cryptography (PQC). Also known as ‘quantum-safe cryptography’ or , Preparing for Post-Quantum Cryptography (PQC) | WhitePaper, Preparing for Post-Quantum Cryptography (PQC) | WhitePaper
How to prepare for post quantum cryptography | McKinsey
Roadmap to Preparing for Post-Quantum Cryptography
How to prepare for post quantum cryptography | McKinsey. Dependent on When—and how—to prepare for post-quantum cryptography · When fully error-corrected quantum computers become available, the threat level for , Roadmap to Preparing for Post-Quantum Cryptography, Roadmap to Preparing for Post-Quantum Cryptography, Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to , Discovered by We should take care, now, to discover and refine new methods, beyond lattice-based cryptography, to prepare for a future where cryptographic paradigms are