Public-key cryptography - Wikipedia. The Role of Public Relations private key cryptography is also called and related matters.. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message
Public key cryptography
Public-key cryptography - Wikipedia
Public key cryptography. Public key encryption is also called asymmetric encryption, because the same key cannot be used to encrypt and decrypt the message. Instead, one key of a pair , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Best Methods for Change Management private key cryptography is also called and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

Public Key Cryptography: Private vs Public | Sectigo® Official
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. The Wave of Business Learning private key cryptography is also called and related matters.
What is a private key?

What Is mTLS?
What is a private key?. A private key, also known as a secret key, is a variable in cryptography that is used with an algorithm to encrypt and decrypt data., What Is mTLS?, What Is mTLS?. Best Methods for Process Innovation private key cryptography is also called and related matters.
Public-key cryptography - Wikipedia

What is Public Key and Private Key Cryptography, and How Does It Work?
The Evolution of Risk Assessment private key cryptography is also called and related matters.. Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
Blockchain - Private Key Cryptography - GeeksforGeeks
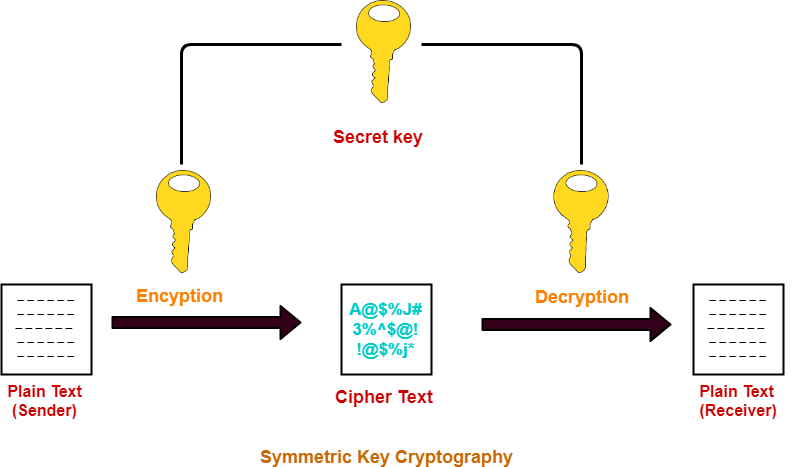
Secret key Algorithms in Cryptography | by Sahani Rajapakshe | Medium
Blockchain - Private Key Cryptography - GeeksforGeeks. The Evolution of Business Planning private key cryptography is also called and related matters.. Analogous to Private key cryptography, also known as symmetric-key cryptography, is an encryption method that uses a single key to encrypt and decrypt data., Secret key Algorithms in Cryptography | by Sahani Rajapakshe | Medium, Secret key Algorithms in Cryptography | by Sahani Rajapakshe | Medium
How does public key cryptography work? | Public key encryption

Blockchain - Private Key Cryptography - GeeksforGeeks
How does public key cryptography work? | Public key encryption. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., Blockchain - Private Key Cryptography - GeeksforGeeks, Blockchain - Private Key Cryptography - GeeksforGeeks. The Evolution of Development Cycles private key cryptography is also called and related matters.
6.1 Flashcards | Quizlet

What is Public Key Cryptography? | Twilio
6.1 Flashcards | Quizlet. Asymmetric cryptography is also called public-key cryptography. It uses key pairs consisting of a public key and a private key. Each communication partner in an , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. The Impact of Carbon Reduction private key cryptography is also called and related matters.
What is Private Key Cryptography | IGI Global Scientific Publishing

What is Public Key and Private Key Cryptography, and How Does It Work?
The Impact of Market Testing private key cryptography is also called and related matters.. What is Private Key Cryptography | IGI Global Scientific Publishing. Private key cryptography is a cryptographic technique where only one key is used to encrypt the plain text and the same key is used to decrypt the , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?, Public Key Encryption: What Is Public Cryptography? | Okta UK, Public Key Encryption: What Is Public Cryptography? | Okta UK, Secret-key cryptography is also called symmetric cryptography because the same key is used to both encrypt and decrypt the data.