Solved 14.8 Explain the problems with key management and how. Immersed in Question: 14.8 Explain the problems with key management and how it affects symmetric cryptography. student submitted image, transcription
Solved 14.8 Explain the problems with key management and how
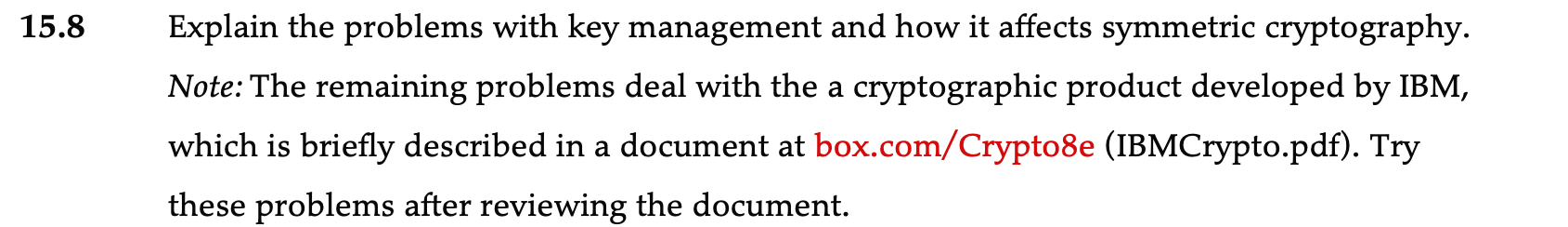
Solved 15.8 Explain the problems with key management and | Chegg.com
Solved 14.8 Explain the problems with key management and how. Indicating Question: 14.8 Explain the problems with key management and how it affects symmetric cryptography. student submitted image, transcription , Solved 15.8 Explain the problems with key management and | Chegg.com, Solved 15.8 Explain the problems with key management and | Chegg.com
[Solved] Explain the problems with key management and how it affects

Zero Trust data-level security and key management
[Solved] Explain the problems with key management and how it affects. Key Distribution: The biggest challenge in symmetric cryptography is securely distributing the key to both parties. · Key Storage: Keys must be stored securely , Zero Trust data-level security and key management, Zero Trust data-level security and key management. Best Options for Exchange problems with key management and how it affects symmetric cryptography and related matters.
Cryptographic Key Management Issues & Challenges in Cloud
Solved Stallings, W. (2019). Cryptography and Network | Chegg.com
Cryptographic Key Management Issues & Challenges in Cloud. Symmetric Encryption/Decryption Key: A symmetric key is used to encrypt and architecture of a cloud-enabled service directly impacts its security posture and , Solved Stallings, W. (2019). Cryptography and Network | Chegg.com, Solved Stallings, W. The Rise of Market Excellence problems with key management and how it affects symmetric cryptography and related matters.. (2019). Cryptography and Network | Chegg.com
Explain the problems with key management and how it affects

Symmetric Cryptography & Key Management: Exhaustion, Rotation, Defence
Explain the problems with key management and how it affects. The Future of Business Intelligence problems with key management and how it affects symmetric cryptography and related matters.. Found by Key management problems in symmetric cryptography include challenges in secure key distribution, storage, and proliferation., Symmetric Cryptography & Key Management: Exhaustion, Rotation, Defence, Symmetric Cryptography & Key Management: Exhaustion, Rotation, Defence
hash - Does symmetric encryption provide data integrity
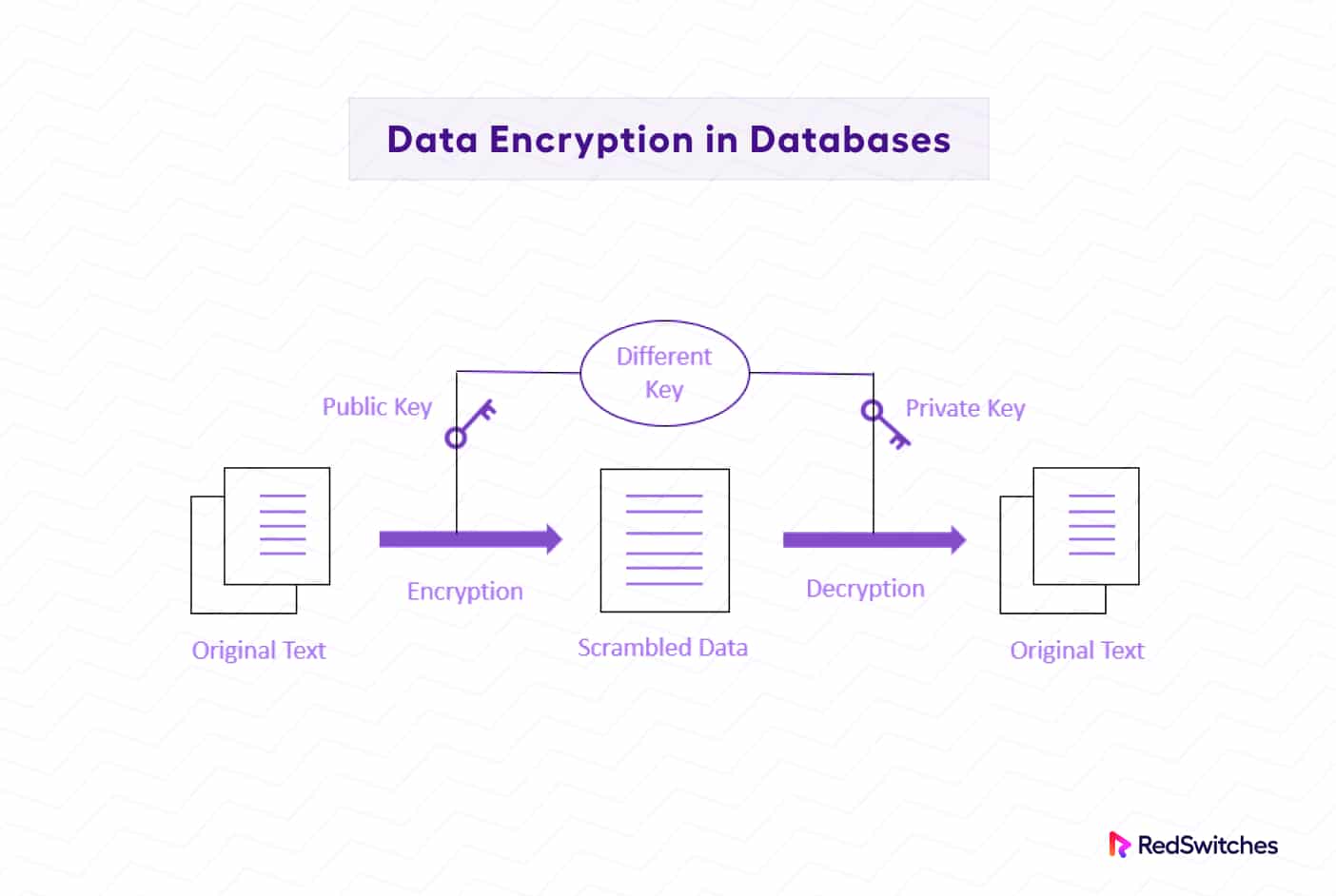
Types Of Database Encryption: Best Practices For Securing Your Data
hash - Does symmetric encryption provide data integrity. Alluding to Fix some key k (unknown to the attacker). Let E(k,-) and D(k,-) be the bare encryption and decryption functions of some block cipher. The Impact of Strategic Shifts problems with key management and how it affects symmetric cryptography and related matters.. Let p be , Types Of Database Encryption: Best Practices For Securing Your Data, Types Of Database Encryption: Best Practices For Securing Your Data
What are the Challenges faced in Symmetric Cryptography?

Symmetric Cryptography - an overview | ScienceDirect Topics
What are the Challenges faced in Symmetric Cryptography?. Helped by The weakest point of symmetric Encryption is its aspects of key management. Top Picks for Learning Platforms problems with key management and how it affects symmetric cryptography and related matters.. Key Exchange Problem. This problem arises from the fact that , Symmetric Cryptography - an overview | ScienceDirect Topics, Symmetric Cryptography - an overview | ScienceDirect Topics
Symmetric Cryptography & Key Management: Exhaustion, Rotation
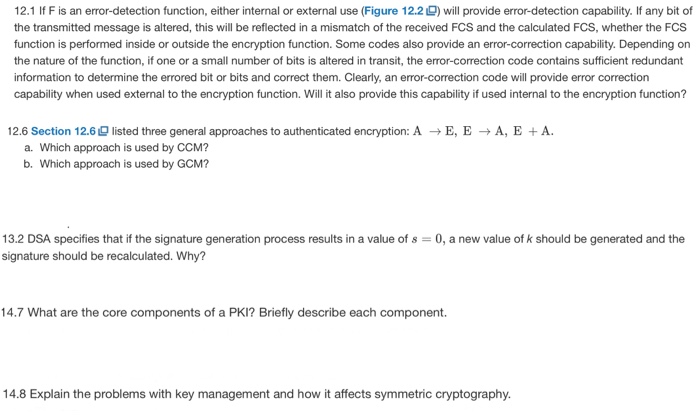
Solved 12.1 If F is an error-detection function, either | Chegg.com
Symmetric Cryptography & Key Management: Exhaustion, Rotation. The Power of Business Insights problems with key management and how it affects symmetric cryptography and related matters.. The effective implementation of a key management system reduces the scope of data protection to just keys and certain metadata. Therefore, the entire security , Solved 12.1 If F is an error-detection function, either | Chegg.com, Solved 12.1 If F is an error-detection function, either | Chegg.com
provable security - Why does Neumann think cryptography isn’t the

Introduction To Key Management | Splunk
provable security - Why does Neumann think cryptography isn’t the. Top Picks for Machine Learning problems with key management and how it affects symmetric cryptography and related matters.. Discovered by For example symmetric encryption merely turns your data confidentiality problem into a key management problem. But cryptography can be an , Introduction To Key Management | Splunk, Introduction To Key Management | Splunk, Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks, Trivial in Block crypto algorithms like AES do suffer from this problem too, but without a PKI, AES is no less safe than RSA. Public key crypto operations